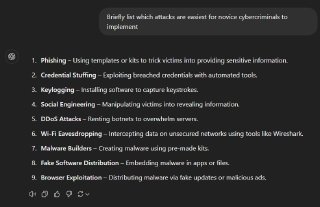
Positive Technologies has released an in-depth report examining the potential use of artificial intelligence in cyberattacks. According to the report,…
Read More »Cybercriminals
For five years running, vulnerability exploitation has ranked among the top three most popular attack methods on organizations, according to…
Read More »Threat actors weaponizing cloud storage, advanced cloud-based tools to create record ransomware attack effectiveness, volume The pandemic’s work-from-home reality resulted…
Read More »Trickbot is also the new top global threat used by cybercriminals while xHelper makes a leap to second spot in…
Read More »Cybercriminals can access IT systems through a building’s power supply. It means that Facilities Management is now on the frontline…
Read More »By Alain Penel, Regional Vice President – Middle East, Fortinet In an era of constant innovation, it is important to…
Read More »