
Six percent of all new valentine’s day related domains found to be malicious; reports Check Point Research
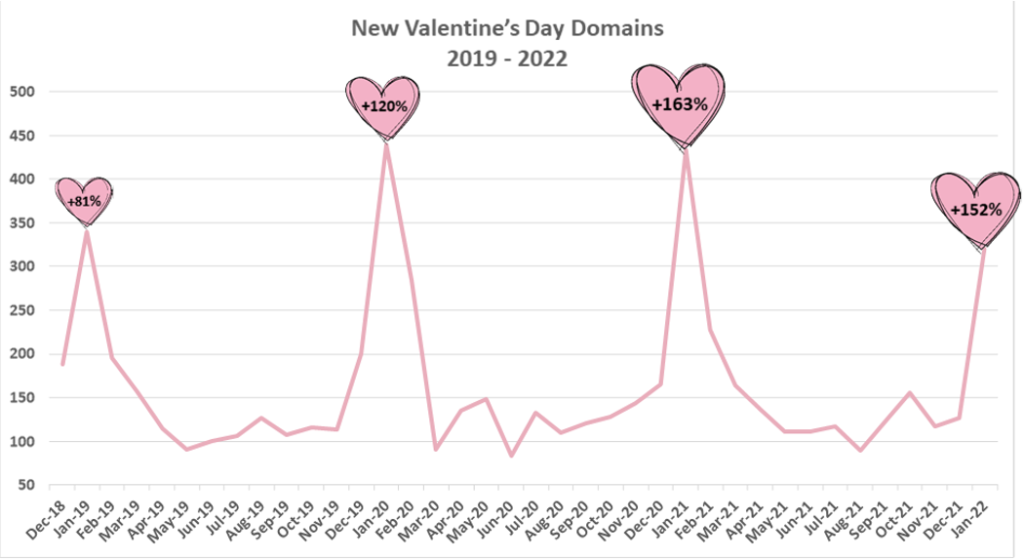
In January this year, Check Point Research witnessed a 152% increase in new domains registered for Valentine’s Day, compared to December 2021. This year, 6% of the new domains were found to be malicious and 55% were found to be suspicious. In the past month, 1 out of every 371 malicious emails were related to Valentine’s Day.
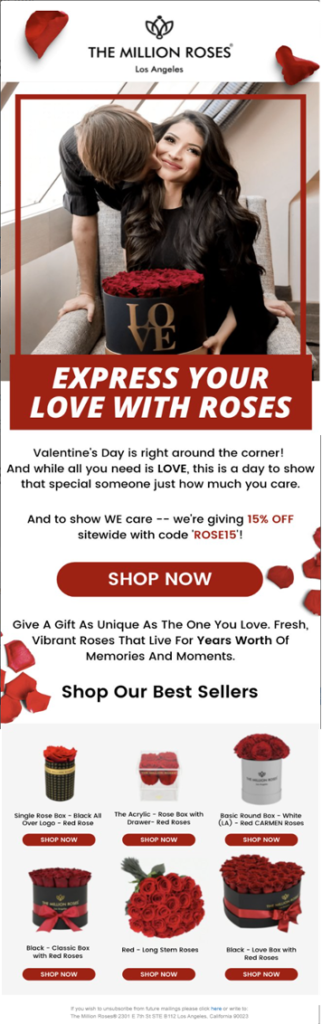
CPR also found an example of a phishing scam focused on buyer fraud. The malicious phishing email used “The Millions Roses” branding to lure victims into purchasing gifts for Valentine’s Day. The fraudulent email (see figure below) was sent from a spoofed address. The fraudulent email listed a company address that was different from the legitimate “The Million Roses” brand. This is a sign that the email is from a dubious source, and the website is fake. Anyone who clicked on the link in the email would have been redirected to a fraudulent malicious link, currently inactive, which tried to imitate “The Million Roses” website.
Phishing attacks occur when malicious actors send messages pretending to be a trusted person or entity. Phishing messages manipulate users into performing actions like installing a malicious file, clicking on a malicious link, or divulging sensitive information such as login credentials. Social engineering is an increasingly common threat vector used in almost all security incidents. Social engineering attacks, like phishing, are often combined with other threats, such as malware, code injection, and network attacks. Furthermore, phishing is the number one cause of ransomware. Since these attacks are specifically designed to exploit the human nature of wanting a good deal, it is extremely important to prevent these attacks from ever reaching their desired victims – because just one “wrong click” can cause tremendous damage.
CPR advices:
- ALWAYS be suspicious of password reset emails: By sending a fake password reset email that directs you to a lookalike phishing site, attackers can convince you to type in your account credentials and send those to them. If you receive an unsolicited password reset email, always visit the website directly (don’t click on embedded links) and change your password to something different on that site (and any other sites with the same password).
- Never EVER share your credentials: Credential theft is a common goal of cyberattacks. Many people reuse the same usernames and passwords across many different accounts, so stealing the credentials for a single account is likely to give an attacker access to a number of the user’s online accounts. As a result, phishing attacks are designed to steal login credentials in various ways
- BEWARE of too good to be true buying offers: as they are really too good and not true… An 80% discount on a new iPhone or an item of jewelry is usually not a reliable or trustworthy purchase opportunity.
- ALWAYS verify you are ordering online from an authentic source: Do NOT click on promotional links in emails, instead Google your desired retailer and click the link from the Google results page.



