
By: Derek Manky, Chief of Security Insights and Global Threat Alliances at FortiGuard Labs
If you were to pick a single word to describe cybersecurity events in recent months, it would be “fast.” FortiGuard Labs has just released the latest semiannual FortiGuard Labs Global Threat Landscape Report, and it indicates that cybercriminals are developing attacks faster than ever. They continue to exploit the expanding attack surface of hybrid workers and IT and are using advanced persistent cybercrime strategies that are more destructive and less predictable than those in the past.
A quick review of four significant takeaways from the threat report
1. Log4j Demonstrates the Speed of Exploits
In December, a critical vulnerability disclosed in the Apache Log4j Java-based logging framework impacted nearly every environment with a Java application. The vulnerability was trivially easy to exploit and gave attackers a way to gain complete control of vulnerable systems. Within days, Log4j became the most prevalent IPS detection in the second half of the year. Shortly after the original disclosure, two other vulnerabilities were discovered that forced organizations to update their Log4j deployments three times in a single week. Despite emerging in the second week of December, exploitation activity escalated quickly enough, in less than a month, to make it the most prevalent IPS detection of the entire second half of 2021. In addition, Log4j had nearly 50x the activity volume in comparison to the well-known outbreak, ProxyLogon, that happened earlier in 2021. Although there were no reports of significant compromises involving the Log4j flaw in the month after it was discovered, it’s possible that attackers exploited the bug to breach networks and are now just waiting for the right time to strike.
2. Adversaries Rapidly Targeting New Vectors – Linux
Not long ago, Linux was one of the least attacked platforms in IT, even though it runs the back-end systems of many networks and container-based solutions for IoT devices and mission-critical applications. However, threat actors are expanding their toolsets and rapidly increasing their use of Linux-based malware. During 2021, malware detections of Executable and Linkable Format (ELF) files, the binary format for Linux, doubled. Additionally, the number of new antivirus (AV) detections Fortinet needed to create quadrupled. The growth in variants and spread suggests that Linux malware is increasing. And with Microsoft actively integrating Windows Subsystem for Linux (WSL) into Windows 11, it’s inevitable that malware will follow. We had ample evidence and reasons to include the continued increase in Linux attacks on our list of 2022 cyber threat predictions.
3. Ransomware Attacks Remain Relentless
The sophistication, aggressiveness, and impact of ransomware continued relentlessly in the second half of 2021. Threat actors continue to attack organizations with a variety of new and previously unseen ransomware strains.
The Kaseya VSA remote monitoring and management technology attack attracted particular attention because of its widespread impact. This incident was another demonstration of the effectiveness of the breach-once-compromise-many nature of software supply chain attacks.
Another troubling trend is the use of old ransomware that’s being actively updated, enhanced, and reused. For example, BlackMatter was used in multiple attacks against U.S. infrastructure, and it is thought to be a rebranding of DarkSide, the ransomware used in the Colonial Pipeline attack. With the enterprise model of Ransomware-as-as-Service, it’s possible for multiple threat actors to distribute malware more easily.
4. Deeper Understanding of Attack Techniques Stops Criminals Faster
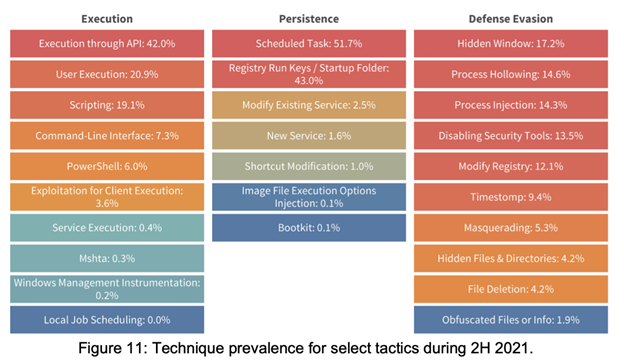
To observe the malicious outcomes of various attacks, FortiGuard Labs analyzed the functionality of detected malware by detonating the malware samples collected. The result was a list of the individual tactics, techniques, and procedures (TTPs) the malware would have accomplished if the attacks had been executed. This high-resolution intelligence shows that stopping an adversary earlier is more critical than ever, and that by focusing on a handful of those identified techniques, in some situations an organization could effectively shut down a malware’s methods for attack.
For example, the top three techniques for the “execution” phase account for 82% of the activity. The top two techniques for obtaining a foothold in the “persistence” phase represent nearly 95% of the observed functionality. Leveraging this analysis can have a dramatic effect in how organizations prioritize their security strategies to maximize their defense.
Smarter Solutions for Better Protection
These attacks are just some of the many we saw in the second half of 2021. As attacks continue to get faster, organizations need to move away from collections of point products to integrated solutions that are designed to work together. To secure against evolving attack techniques, organizations need smarter solutions that can ingest real-time threat intelligence, detect threat patterns and fingerprints, correlate massive amounts of data to detect anomalies, and automatically initiate a coordinated response. The centralized management and broad visibility of a cybersecurity mesh platform can help ensure that policies are enforced consistently, configurations and updates are delivered promptly, and a coordinated threat response can be launched when suspicious activity is detected.
The FortiGuard Labs Threat Landscape Report Overview
The latest Global Threat Landscape Report represents the collective intelligence of FortiGuard Labs. Its data is drawn from the Fortinet array of sensors that collect the billions of threat events observed worldwide. Using the first three groupings of reconnaissance, resource development, and initial access from the MITRE ATT&CK framework, the FortiGuard Labs Global Threat Landscape Report classifies adversary tactics and techniques to describe how threat actors find vulnerabilities, build malicious infrastructure, and exploit their targets. The report also covers global and regional perspectives to provide security professionals with broad and specific insight into the threat landscape, empowering them to make decisions calculated to reduce their risks and better protect and preserve their critical digital resources.




