
By Gal Yogev, Cyber Security Researcher at Check Point Software Technologies
Check Point Research researchers have identified numerous Facebook pages playing host to these hacker groups, aiding the exchange and trade of phishing-related resources.
Every phishing attack aims to masquerade as a trustworthy site, associated with a well-known brand, and trick unsuspecting victims into sharing their personal data and credentials. However, it requires a specific skill set and considerable time to create a convincing landing page.
There exists a wide array of tools that can help in creating a decent replica of popular brands such as Netflix, Facebook, and Microsoft. However, there is a lack of free or inexpensive tools that can replicate lesser-known or local brands.
A common deceptive technique employed by cybercriminals, brand phishing also known as brand impersonation or brand spoofing, is used to impersonate known brands or organizations to steal valuable data for later scams. By taking on the identity of a known brand, the attacker can trick the recipient into clicking on a malicious link or opening a virus-infected email attachment, exploiting the brand’s trust to manipulate the victim into revealing sensitive data or becoming a victim of malicious activities.
Let’s consider an instance where an attacker wants to phish for customer credentials at a local bank in Saudi Arabia. The attacker would need to construct an exact replica of the bank’s login page, set up a convincing domain, upload the webpage to a host, and finally build the backend infrastructure to handle the receipt and storage of stolen credentials. Although this might not pose a significant challenge for a skilled Full Stack developer, it could prove a difficult task for an average internet user.
As with any technical problem, the obvious solution lies in outsourcing.
Reputable developers are likely to refuse to construct phishing pages, so the search must focus on developers with fewer scruples. The Darknet might seem the best place to look for such developers, but a simpler option exists: Facebook.
Like countless other subjects, Facebook hosts numerous groups for different interest groups, with some of them being hackers and scammers. These public groups have thousands of members who buy, sell, and trade phishing pages, credit card data, hacking tools, and much more.
In the following post, we see a malicious actor advertising not only the phishing page but also a complete 2FA bypass process, which can facilitate significant theft from victims. The advertiser provides multi-language support and seems to be a professional scammer.
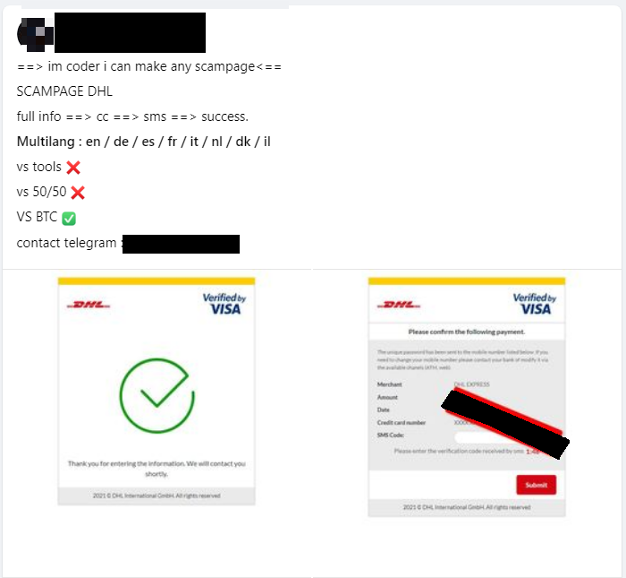
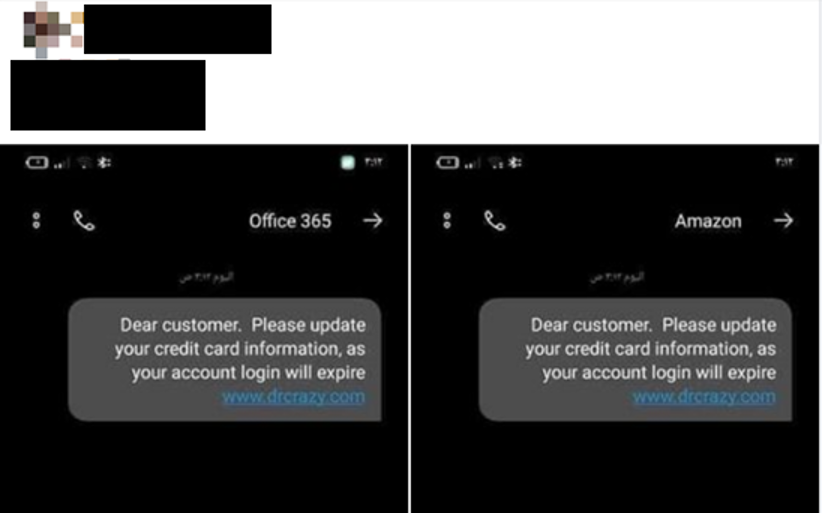
However, owning a phishing page is not enough; the phishing page URL must somehow reach the intended victim. Thankfully, many solutions for this exist in the same Facebook groups. For instance, we find another attacker offering SMS services, which can spoof any brand and deliver the message to potential victims.
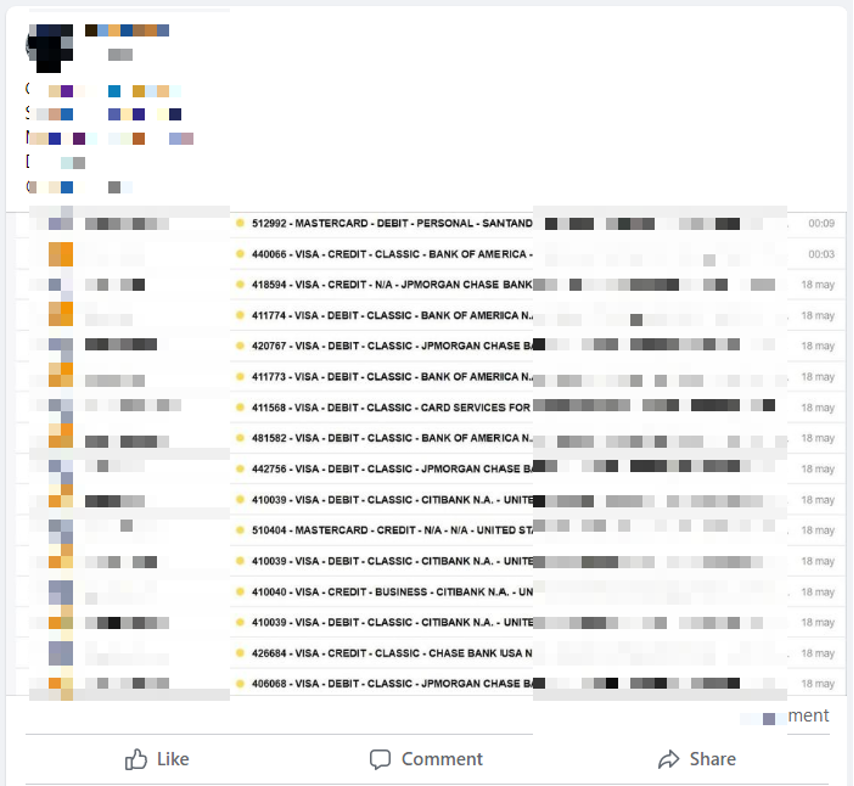
What happens to all the stolen credit card information? Some of it is bulk resold by the attackers for a handsome profit.
This activity, commonly associated with the hidden corners of the Darknet, actually takes place openly and is accessible to anyone wishing to execute phishing attacks, regardless of their skill level.
As phishing attacks become more advanced and common, having dependable anti-phishing tools is essential for any organization or individual who could suffer serious damage due to credential leaks.
Five Strategies to Safeguard Your Organization from Phishing Attacks
Here are some practical ways to lower the risk of phishing attacks in your organization:
1. Utilize Endpoint Monitoring and Protection:
With the increasing use of personal devices and cloud services at work, several new endpoints have been introduced that might be vulnerable. Security teams need to assume that some endpoints will inevitably be breached. Therefore, it is critical to monitor these endpoints for security threats and implement quick remediation on compromised devices.
2. Conduct Phishing Attack Tests:
Simulated phishing attacks can help gauge the effectiveness of your security awareness training programs and help users better comprehend attacks. Regular testing is essential to mimic real phishing attacks as the threat landscape continuously evolves.
3. Limit User Access to Sensitive Systems and Data:
Most phishing techniques are designed to trick humans, and privileged user accounts are prime targets for cybercriminals. By limiting access to systems and data, you can help prevent sensitive data leaks. Adopt a policy of least privilege, granting access only to those who absolutely need it.
4. Deploy Email Security Solutions:
Modern email filtering solutions can shield against malware and other malicious content in email messages. These solutions can identify emails containing malicious links, attachments, spam, and language indicative of a phishing attack. They automatically block and quarantine suspicious emails and employ sandboxing technology to scrutinize if emails contain malicious code.
5. Employee Awareness Training:
Teaching employees to understand phishing strategies, identify signs of phishing, and report suspicious activities to the security team is paramount. Encourage employees to look for trust badges or seals from recognized cybersecurity or antivirus companies before interacting with a website. This shows the website is serious about security and is likely not fraudulent or harmful.
Check Point Customers are protected against phishing attacks
Check Point’s 360° Anti-Phishing solutions eliminate potential threats across email accounts, browsers, endpoints, mobiles and networks.Powered by ThreatCloud AI, our Zero-day phishing protection analyzes hundreds of indicators of compromise in real time, in order to identify and block new and known phishing sites. . ThreatCloud AI analyzes the characteristics of the URL and webpage and to determine whether there is a phishing threat and also eliminates risk from incoming emails by inspecting all aspects of messages before they enter the mailbox, including attachments, links and email text. Check Point 360° Anti-Phishing solutions powered by ThreatCloud AI’sZero-Day phishing engine, blocks four times more attacks when compared to signature-based technologies. Our solutions have a 40% higher catch rate when compared to other AI based cyber security technologies.




